Digital protection for the Red Cross
Five years ago, the Centre for Cyber Trust and the International Committee of the Red Cross (ICRC) began exploring the concept of a digital emblem to protect against cyberattacks. Now, a working group within the Internet Engineering Task Force is standardising a solution—representing a major step forward in this ambitious project.
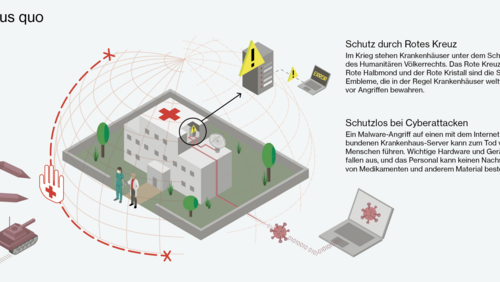
The Red Cross, possibly the most recognised and trusted symbol in the world. It is the emblem of the Red Cross Movement and, for the past one hundred and sixty years, has served as a protective sign in armed conflicts by designating as protected affiliated hospitals, ambulances, medical supplies and aid as well as medical staff and humanitarian aid workers.
In the digital sphere, however, no corresponding symbol exists that would inform cyber operators—be they military or civilian actors—that they’re attacking the digital infrastructure of a humanitarian institution. Five years ago, the International Committee of the Red Cross (ICRC) initiated a research project to explore the concept of a protective digital emblem for the Red Cross, Red Crescent and Red Crystal.
In an intermediary report on the project, the ICRC states that digital emblems are not intended to replace cyber defence systems. Rather, the idea is for them to prevent cyberattacks on institutions and facilities conducted by actors who would otherwise not target a humanitarian organisation. That such attacks do indeed occur is something the ICRC knows from bitter experience: at the start of 2022, for example, ICRC servers containing the personal data of more than half a million people were hacked.
From idea to standard
Since the project’s start, the academic partner in the ICRC project has been the WSS-funded Centre for Cyber Trust at ETH Zurich and the University of Bonn. During the project’s first phase, the researchers developed a technical solution, the Authentic Digital Emblem (ADEM), to implement the idea. Their development convinced the ICRC to continue pursuing their proposal.
The project has now taken a significant step towards deploying the concept: a working group has been formed in the Internet Engineering Task Force (IETF) to focus on developing a technical standard for a protective digital emblem, where the first meeting took place in July 2025. The IETF is an international organisation whose participants are volunteers—software developers, network service providers and researchers—who develop standards through open, inclusive processes to ensure the internet functions smoothly.
“It’s fantastic that our project has progressed so far,” says David Basin, head of the ETH Zurich Institute of Information Security and co-leader of the Centre for Cyber Trust. His praise is directed mainly towards his postdoc Felix Linker. While writing his PhD thesis, Linker was largely responsible for developing and advancing ADEM, and he’s now in charge of technical aspects in the IETF working group.


Helping hackers
“What makes our project unique is that the end users are hackers,” Linker says. “Our job is to anticipate their needs.” And because hackers will conceal their intentions at all costs, the digital emblem shouldn’t set off an alarm or leave traces when they access a system. “We want to place our symbol in such a way that it enables hackers to conduct a kind of covert inspection,” he explains.
When he says “place”, he doesn’t mean putting the Red Cross symbol on a website. “One reason is that not every digital resource has a human-operated interface the way a website does,” Linker says, adding that patient databases would be one example of this. Another reason is that cyberattacks are generally automated processes—as a rule, a script is run to seek vulnerabilities in a system’s design.
Rather than using a physical symbol, “placing” the protective emblem involves adding code into an internet protocol that governs communication between two devices. The first option the IETF working group is exploring is inserting the emblem into the Domain Name System (DNS). DNS essentially functions as the internet’s telephone book, linking domain names (such as “www.google.com”) with specific information. The most important DNS links contain IP addresses that enable a browser to find the right website, as Linker explains. “But it’s also possible to connect other information with domain names in the DNS—in our case, digital emblems.”
Simple processes
In a later phase, the group also plans to develop alternatives for placing the emblems: on servers, for example, or in the Internet Control Message Protocol (ICMP) used to report and resolve network errors. However, Linker stresses that the number of possible placements should be kept to a minimum. “The process must be simple. Hackers don’t want to check twenty different places to see if there might be a protective emblem somewhere.”
This means scripts written by hackers must be able to detect an emblem quickly and easily. At the same time, however, the emblem shouldn’t impede the flow of data on the internet. The developers also want to avoid an integration solution for apps that would require updating a software program with millions of users, as this would be too complicated and too expensive.
In its report, the ICRC also discusses the potential risks of using digital emblems. First and foremost, self-identification could endanger humanitarian operations and data by drawing the attention of bad actors in the first place—this problem also applies to physical protective signs, as Felix Linker points out. “That’s why we want to design the digital emblem as an offer. Affected persons and organisations should be able to use it to identify themselves, but they could also remove it, if desired.”
Technology plus policy
The IETF group is currently addressing these challenges. Felix Linker says it’s hard to say how long it will take the members to agree on a solution. There are also ongoing discussions about whether the project should be expanded to include other emblems—for journalists, for example, or internationally protected wetlands. Depending on the answers, Linker estimates the work will take between one and three years. Nevertheless, technical developments for implementation will continue while the discussions take place.
In addition to technical aspects, policy-related measures are also critical. Before entering into legal force, the digital emblems for the Red Cross, Red Crescent and Red Crystal must be adopted in international humanitarian law; this step is also the only way to prevent the emblems from being misused. In previous publications, the ICRC has discussed several mechanisms to achieve this: one possibility would be to append a new protocol to the Geneva Conventions, similar to the 2005 procedure for introducing the Red Crystal symbol, and another would be to amend Annex I to Protocol Additional I, which regulates the use of radio and light signals for identification.
In either case, the digital emblems would also have to be incorporated into national legislation and enforced by national authorities, as is currently the case for the physical protective signs. The ICRC says it has already begun talks with nations to find the best path forward.
Tested by NATO
How far the system has progressed is also evidenced by a very recent event. At the start of November 2025, NATO’s Cooperative Cyber Defence Centre of Excellence (NATO CCDCOE) in Tallinn, Estonia, tested ADEM as part of a larger exercise. For the tests, the researchers used their DNS approach to link an emblem to potential targets of cyberattacks. “Our goal was to test whether our prototype and the current design can be easily integrated into the work of a cyber commando,” Linker explains.
While he can’t discuss the results of the exercise, he’s certain that the results will be extremely useful for the project’s further development: “We’re expecting valuable feedback for ADEM’s design.” The manoeuvre also served another purpose: standardisation processes at IETF require that all groups involved demonstrate their interest in a solution. The NATO cyber commando exercise has now made clear that parties who seek the emblem during cyber operations—whether offensive or defensive—have this interest.
It will admittedly take some time before the protective signs become a standard feature in digital spaces. Nevertheless, David Basin and Felix Linker are optimistic that at some point in time the ADEM solution created at the Centre for Cyber Trust will make the world a safer place.